The AzureIP scanner is a very powerful tool. Time to look at some new features. And the option to decrypt an Office document on download.
Azure Information Protection scanner
It was somewhere in 2017 that I was able to look at the Azure Information Protection Scanner for the first time. It was still in preview, but I really liked the possibilities this scanner provided.
One of the more recent versions of the scanner provides us with more options to scan the on-premise fileshares and SharePoint environments. And I wanted to show you some of these.
Multiple repositories

Using the Add-AIPScannerRepository cmdlet you can add one or more locations to scan. There are some additional options now available. And these work per repository, which is very nice. As shown in the figure above. One of the more powerful (I think) is the ability to set a default label. Please note that:
- This default label can be based on the policy or a specific label;
- The default label can be based on the repository.
So now you can label any information in a confidential SharePoint library with a different label, for example. You will need to set the -MatchPolicy parameter to Off. In this example I set my default policy to General and used this setting.

Using the cmdlet Set-AIPScannerScannedFileTypes you can determine which files need to be scanned and which can be skipped. In the example above you’ll notice that the first location excludes the default list of extension. The other location is set to scan all files, which uses this parameter: @(“*”)
Using this cmdlet you can add these file types to specific repositories. As AzureIP is not designed to protect all document types, please use restraint when using this cmdlet.
If you want to know if there is any sensitive information in the on-premise information, you can now use the Set-AIPScannerConfiguration cmdlet with the -DiscoverInformationTypes parameter. Set this to All and the discovered information types show up in the logfiles.
Decrypt on download
When using Office 365 message encryption any e-mail is encrypted and/or additionally protected using rights management. Any Microsoft Office document contained in this e-mail is protected using the same encryption. Recipient(s) of this e-mail need to have an Microsoft Office account to be able to open it. And this account needs to have the same e-mail address as used in the e-mail.
Long story short: people don’t understand and attachments cannot be opened. Especially when people are sending protected e-mails to non-Microsoft accounts or people with a out-of-date version of Microsoft Office.
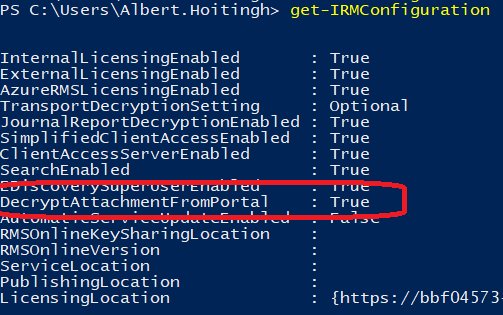
But this has been modified by Microsoft. You can now set IRM configuration (on tenant level) to allow the document to be decrypted when downloaded. The e-mail and attachments are still encrypted in transit, but this encryption is removed when the document is downloaded.
Please note:
- this is only possible when the “Encrypt only” option is used. When you use any rights management policy (for example – do not forward), the recipient still needs to have an Microsoft Office account to open the document.
- this is not applicable to your Office 365 users. They will still consume the encrypted content.
Just so you know 🙂
One comment